As of the latest versions, Ninox On-Premise 3.12.8 and Ninox 3.13.0 do not natively support custom LDAP filters or query criteria. However, the underlying package, “node-activedirectory” does support LDAP filters. With a few minor code modifications, you can enable this functionality.
The Challenge and the Solution
By default, Ninox does not provide an option to configure custom LDAP filters directly. This limitation can be a roadblock if you need to implement specific criteria for user authentication. Fortunately, with a slight tweak to the code, we can harness the power of the “node-activedirectory” package to add this capability.
Modifying the Configuration
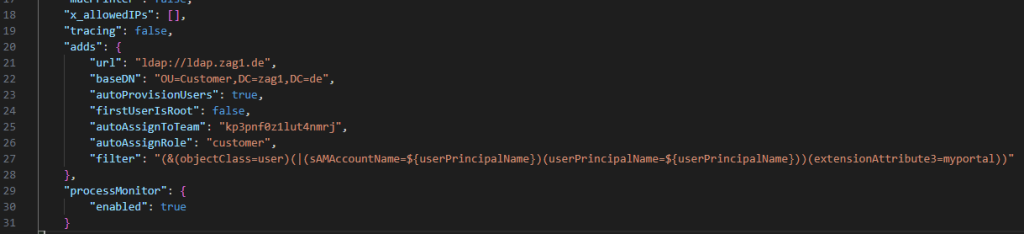
To enable custom LDAP filters, we made some adjustments to the server configuration file. Here’s a snapshot of our modified server-config.json:
{
"data": "C:/ProgramData/Ninox",
"ssl": false,
"host": "blog.zag1.de",
"port": 443,
"bindPort": 8080,
"bindInterface": "0.0.0.0",
"emailHost": "smtp.zag1.de",
"emailPort": "25",
"emailSecure": false,
"emailUser": "relay@smtp.zag1.de",
"emailPassword": "",
"emailFrom": "info@zag1.de",
"snapshots": true,
"hideUserList": true,
"synclog": false,
"macPrinter": false,
"x_allowedIPs": [],
"tracing": false,
"adds": {
"url": "ldap://ldap.zag1.de",
"baseDN": "OU=Customer,DC=zag1,DC=de",
"autoProvisionUsers": true,
"firstUserIsRoot": false,
"autoAssignToTeam": "kp3pnf0z1lut4nmrj",
"autoAssignRole": "customer",
"filter": "(&(objectClass=user)(|(sAMAccountName=${userPrincipalName})(userPrincipalName=${userPrincipalName}))(extensionAttribute3=myportal))"
},
"processMonitor": {
"enabled": true
}
}Applying the LDAP Filter
The key modification is the addition of the LDAP filter in the adds.js section. This filter restricts user accounts to those where the extensionAttribute3 is set to myportal.
Here’s how we implemented the changes in the code:
// #################################################################################
// 2024-07-23 Added LDAP-Query option
//
var ldapOpts = {
// addsConfig.filter is *OPTIONAL* and should always include at minimum:
// - (objectClass=user)
// - (anything=${userPrincipalName})
// additional criterias are possible, like the following:
// "(&(objectClass=user)(|(sAMAccountName=${userPrincipalName})(userPrincipalName=${userPrincipalName}))(extensionAttribute3=myportal))"
//
filter: addsConfig.filter,
scope: 'sub'
};
const ldapOptsReplacements = {
userPrincipalName: accountName
};
if (ldapOpts.filter != null && ldapOpts.filter != undefined) {
// Perform replacements
for (let key in ldapOptsReplacements) {
ldapOpts.filter = ldapOpts.filter.replace(new RegExp(`\\$\\{${key}\\}`, 'g'), ldapOptsReplacements[key]);
}
}
else {
ldapOpts = null;
}
// #################################################################################Conclusion
With these modifications, Ninox On-Premise can now support custom LDAP filters, allowing for more tailored and secure user authentication processes. If you need further assistance or details, feel free to contact us at info@zag1.de.
Stay tuned for more updates and tips on enhancing your Ninox experience!